Patching automation register
P.Leclercq in Security 2025-10-03 governance security tips

To continue documenting security actions, here is a simple example of an automatic patching configuration register.
P.Leclercq in Security 2025-10-03 governance security tips

To continue documenting security actions, here is a simple example of an automatic patching configuration register.
P.Leclercq in Security 2025-09-21 technology security tips

In a world where cyber threats evolve rapidly, regularly updating systems is essential to protect your data. Security patches close vulnerabilities exploited by hackers, but applying them manually can be tedious and often overlooked. Automating this process is therefore an effective solution to ensure continuous protection. This is the reason why it is the second recommendation in the Cybersecurity Fundamentals Small, and is present in all the main security frameworks.
P.Leclercq in Security 2025-08-01 governance security tips

Before delving further into Cyberfundamentals, we’ll address an issue that isn’t explicitly listed in the texts, but which is fundamental to meeting the following requirements: asset inventory. Indeed, “how do you protect what you don’t know?” is a well-known saying in security.
P.Leclercq in Security 2025-07-26 governance security tips
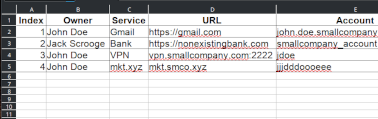
When we talk about security and compliance, we must also talk about documentation. It’s important to keep a list of actions to be taken, their progress, and their results throughout the lifecycle of an initiative.
P.Leclercq in Security 2025-07-05 technology security tips

Using the same password across multiple accounts might seem convenient, but it’s one of the biggest security risks you can take. Here’s why unique passwords and a password manager are essential for your business survival.
P.Leclercq in Security 2025-06-21 technology security tips

Here’s a step-by-step guide to enabling two-factor authentication (or two-step verification) on your Google Account, along with instructions on how to use it once set up. This feature strengthens your account’s security by adding an extra step when logging in. This will prevent an imposter from logging in to your account even if they’ve stolen your username and password.
P.Leclercq in Security 2025-06-08 governance technology security tips

Two-factor authentication is a security method that requires two distinct forms of identification to access an account or system. Unlike traditional password-only authentication, 2FA adds an additional layer of protection.
P.Leclercq in Security 2025-05-27 governance

As mentioned in a previous article, security begins with governance. Management must indicate its commitment to protecting information, set objectives, and describe the means to be implemented. Traditionally, this is done through a document: the cybersecurity policy.
P.Leclercq in Security 2025-05-06 governance

In the previous article, we listed the basic practical measures to implement to achieve a minimum level of security. However, it is crucial to understand that your company’s security doesn’t begin with technology, but with governance. Installing antivirus software or enabling two-factor authentication will have only a limited impact if you haven’t first clearly defined who makes decisions, according to what rules, and based on what risks.
P.Leclercq in Security 2025-04-24 security tips governance

According to its creator, the Centre for Cybersecurity Belgium (CCB), “The CyberFundamentals Framework is a set of concrete measures to protect data, significantly reduce the risk of the most common cyber-attacks, and increase an organisation’s cyber resilience.”