2FA register
P.Leclercq in Security 2025-07-26 governance security tips
Why keeping registers is essential for your company’s security
When we talk about security and compliance, we must also talk about documentation. It’s important to keep a list of actions to be taken, their progress, and their results throughout the lifecycle of an initiative.
A register allows you to:
- plan and estimate efforts, measure progress, identify gaps, omissions, and redundancies, and facilitate coordination between stakeholders;
- keep track of all changes made and reconstruct the chronology of events. This speeds up diagnosis and strengthens incident response capacity;
- analyze what worked well or poorly over time, with a view to continuous improvement;
- prove to third parties, for example during compliance audits, that actions were actually implemented. Certain standards (Cyber Fundamentals, ISO 27001, NIST, GDPR, DORA, etc.) require documented evidence.
2FA register
We will therefore apply this best practice by creating a register to track the implementation of two-factor authentication. This register can take various forms: a sheet of paper or notebook, a computer file in text format, a spreadsheet, a database…
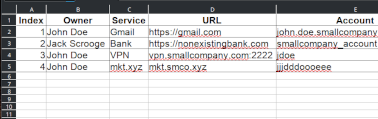
Here is a simple layout example. You can obviously modify it according to your own needs.
| Index | Owner | Service | URL | Account | Status | Method | Activation date | Note |
|---|---|---|---|---|---|---|---|---|
| 1 | John Doe | Gmail | https://gmail.com | john.doe.smallcompany@gmail.com | Done | SMS | 01/02/25 | OK |
| 2 | Jack Scrooge | Bank | https://nonexistingbank.com | smallcompany_account | Ongoing | OTP token | Awaiting confirmation |
You can download an example spreadsheet here.
Of course, keep it in a safe place; it contains sensitive credentials.
Conclusion
In summary, a register is not a simple administrative formality. It is a strategic lever that strengthens the vigilance, responsiveness, and credibility of your IT security approach.