Patching automation register
P.Leclercq in Security 2025-10-03 governance security tips

To continue documenting security actions, here is a simple example of an automatic patching configuration register.
P.Leclercq in Security 2025-10-03 governance security tips

To continue documenting security actions, here is a simple example of an automatic patching configuration register.
P.Leclercq in Security 2025-08-01 governance security tips

Before delving further into Cyberfundamentals, we’ll address an issue that isn’t explicitly listed in the texts, but which is fundamental to meeting the following requirements: asset inventory. Indeed, “how do you protect what you don’t know?” is a well-known saying in security.
P.Leclercq in Security 2025-07-26 governance security tips
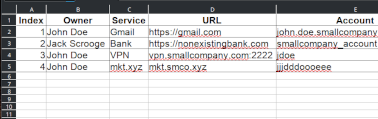
When we talk about security and compliance, we must also talk about documentation. It’s important to keep a list of actions to be taken, their progress, and their results throughout the lifecycle of an initiative.
P.Leclercq in Security 2025-06-08 governance technology security tips

Two-factor authentication is a security method that requires two distinct forms of identification to access an account or system. Unlike traditional password-only authentication, 2FA adds an additional layer of protection.
P.Leclercq in Security 2025-05-27 governance

As mentioned in a previous article, security begins with governance. Management must indicate its commitment to protecting information, set objectives, and describe the means to be implemented. Traditionally, this is done through a document: the cybersecurity policy.
P.Leclercq in Security 2025-05-06 governance

In the previous article, we listed the basic practical measures to implement to achieve a minimum level of security. However, it is crucial to understand that your company’s security doesn’t begin with technology, but with governance. Installing antivirus software or enabling two-factor authentication will have only a limited impact if you haven’t first clearly defined who makes decisions, according to what rules, and based on what risks.
P.Leclercq in Security 2025-04-24 security tips governance

According to its creator, the Centre for Cybersecurity Belgium (CCB), “The CyberFundamentals Framework is a set of concrete measures to protect data, significantly reduce the risk of the most common cyber-attacks, and increase an organisation’s cyber resilience.”
P.Leclercq in Security 2023-08-06 governance

As noted on the main page of this site, I have written an introduction to the European GDPR regulation, which should be sufficient for you to pass the GDPR Foundation exam. It is available as a download here.
P.Leclercq in Security 2023-08-06 governance ISO27001

As noted on the main page of this site, I have written an introduction to the ISO 27001:2013 standard, which should be sufficient for you to pass the ISO 27001 Foundation exam.
You can download it from here.