Email and envelope headers
P.Leclercq in Security 2024-02-22 technology

Email and envelope headers
Interpreting email headers is an essential skill when dealing with email-related issues or investigating the source of an email. Email headers contain valuable information about the path an email took from the sender to the recipient. It allows debugging email issues like non-delivery and detecting fraud or phishing.
In this article, we will learn how to interpret the basic data of email headers.
What are email headers?
An email has more raw content than what your email client (Outlook, Gmail, Thunderbird or your webmail interface) shows you. The various actors sending, transporting and receiving your email add content to it along its way. These data are contained in a set of lines at the top of the email, above the content, called the headers.
Note
The original definition of the email header in RFC 822 calls the whole set of headers “the header”, composed of fields. The more recent RFC 2076 calls the set of headers “heading” and each separate entry a header. In the following text, we will follow this latest convention.
A header is composed of a header name, a colon (:) and header value(s).
A reminder about SMTP
In another previous article, we have explained the SMTP protocol.
Remember: the transmission of an email from a User Agent (MUA or mail client) to an email relay (MTA) occurs via the following dialog:
HELO/EHLO: used by the client to identify itself;MAIL FROM: used by the client to identify the sender;RCPT TO: used by the client to identify the recipient;DATA: introduces the real content of the email. The end of the data is marked by a line only containing a sigle dot (“.”).QUIT: closes the conversation.
Envelope and email
You can consider that the content transmitted by the various components handling your email is divided in two parts.
Part 1: the envelope
The envelope shows data needed to transport your email. In the traditional mail, this is the equivalent of what is written on the outside of the envelope you put your letter in.

There is:
- the name and postal address of the recipient;
- the name and postal address of the sender, that can be used by the postal service to return the mail if it cannot be delivered;
- the stamp of the postal services that transported your mail. Each post office could add its stamp.
Note that the postal service will not (normally) open the envelope.
The HELO/EHLO, MAIL FROM and RCPT TO are the envelope headers, belonging to the SMTP layer. They may be altered during the email’s journey.
Part 2: the mail itself
Inside the envelope, there is a letter with the actual content you want your addressee to read.
The email part is similar, and appears after the DATA tag in the SMTP conversation.
A minimal set of email headers will contain:
From:orReply-To:the sender’s addressTo:the recipient’s email addressDate:when it was sent
A minimal example
We will send a very simple message directly via telnet (without email client) to a mail server.
telnet mailserver 25
Trying 192.168.50.214...
Connected to mailserver.int.osix.be.
Escape character is '^]'.
220 mailserver ESMTP Postfix (Debian/GNU)
HELO gandalf
250 mailserver
MAIL FROM: Jack.Smith@mydomain.com
250 2.1.0 Ok
RCPT TO: pleclercq@mydomain.com
250 2.1.5 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
Test.
.
250 2.0.0 Ok: queued as 4B76334DA
QUIT
221 2.0.0 Bye
Connection closed by foreign host.
The complete source of the received message is:
From - Sun Feb 25 16:48:01 2024
X-Account-Key: account7
X-UIDL: 0000000e65454373
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
X-Mozilla-Keys:
Return-Path: <Jack.Smith@mydomain.com>
X-Original-To: pleclercq@mydomain.com
Delivered-To: pleclercq@mydomain.com
Received: from gandalf (unknown [192.168.50.31])
by mailserver (Postfix) with SMTP id 4B76334DA
for <pleclercq@mydomain.com>; Sun, 25 Feb 2024 16:46:36 +0100 (CET)
Test.
The envelope headers are minimal:
- RFC 5321 mandates that the
MAIL FROMvalue is copied by the final MTA into a header, usually theReturn-Path:one. It is the case here. - The final MTA has also set the
Delivered-Toheader to the recipient’s address. - A
Received:header has been added by the mail server, containing the name and IP address of the sending machine (gandalf, 192.168.50.31), the name of the receiving machine (mailserver), the recipient’s address and a timestamp. If there are several hops, each MTA will add its ownReceived:header to trace the email journey.
As explained earlier, these envelope headers show the ‘transport’ part of the protocol.
The mail headers themselves are absent. There are no From:, To: or Subject: mail headers since they were not present in the DATA part.
The X-headers are proprietary, non official data used by the email client and server software.
This is how it is displayed at the recipient’s end:
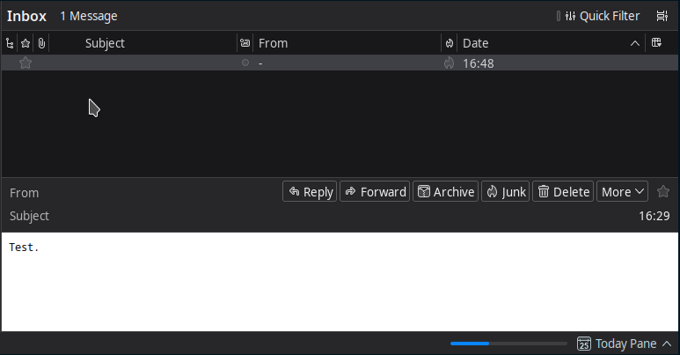
There are no From, To and Subject fields in the DATA area, so the email client cannot copy them and leaves them blank.
A more complete example
Let’s send a more complete email with From:, To: and Subject: fields in the DATA section.
telnet mailserver 25
Trying 192.168.50.214...
Connected to mailserver.int.osix.be.
Escape character is '^]'.
220 mailserver ESMTP Postfix (Debian/GNU)
HELO gandalf
250 mailserver
MAIL FROM: Jack.Smith@mydomain.com
250 2.1.0 Ok
RCPT TO: pleclercq@mydomain.com
250 2.1.5 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
From: Jack.Smith@mydomain.com
To: pleclercq@mydomain.com
Subject: Test email
Test.
.
250 2.0.0 Ok: queued as 8FCE834DA
QUIT
221 2.0.0 Bye
Connection closed by foreign host.
The complete source of the received message is:
From - Sun Feb 25 16:54:08 2024
X-Account-Key: account7
X-UIDL: 0000000f65454373
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
X-Mozilla-Keys:
Return-Path: <Jack.Smith@mydomain.com>
X-Original-To: pleclercq@mydomain.com
Delivered-To: pleclercq@mydomain.com
Received: from gandalf (unknown [192.168.50.31])
by mailserver (Postfix) with SMTP id 8FCE834DA
for <pleclercq@mydomain.com>; Sun, 25 Feb 2024 16:52:06 +0100 (CET)
From: Jack.Smith@mydomain.com
To: pleclercq@mydomain.com
Subject: Test email
Test.
The From:, To: and Subject: email headers have now been filled with the corresponding fields from the DATA part.
This is now how it is displayed at the recipient’s end:
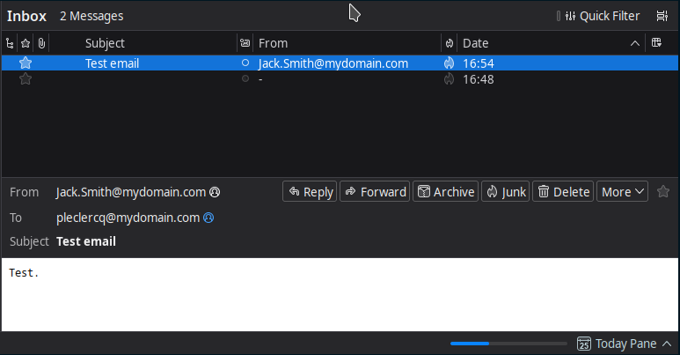
The fields displayed in the email client have been extracted from the email headers.
An example with email client
Let’s now use a regular email client to send a mail.
These are the settings for the sender’s email client:
This is the composed email:
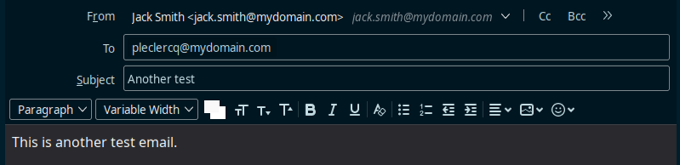
And the complete content:
From - Sun Feb 25 16:59:03 2024
X-Account-Key: account7
X-UIDL: 0000001065454373
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
X-Mozilla-Keys:
Return-Path: <jack.smith@mydomain.com>
X-Original-To: pleclercq@mydomain.com
Delivered-To: pleclercq@mydomain.com
Received: from [192.168.50.31] (unknown [192.168.50.31])
by mailserver (Postfix) with ESMTP id AD50834DA
for <pleclercq@mydomain.com>; Sun, 25 Feb 2024 16:58:48 +0100 (CET)
Message-ID: <a5022c36-ee41-448a-9864-d13cfacc97bb@mydomain.com>
Date: Sun, 25 Feb 2024 16:58:48 +0100
MIME-Version: 1.0
User-Agent: Mozilla Thunderbird
Content-Language: en-GB
To: pleclercq@mydomain.com
From: Jack Smith <jack.smith@mydomain.com>
Subject: Another test
Content-Type: text/plain; charset=UTF-8; format=flowed
Content-Transfer-Encoding: 7bit
This is another test email.
This is how it is received:
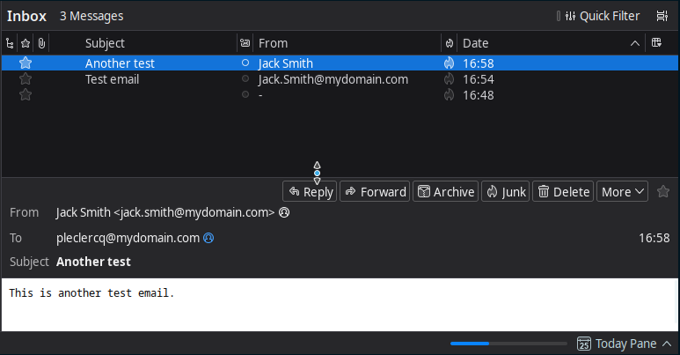
Again, the fields in the email client have been filled from the From:, To: and Subject: headers. The From: header has a more complete look, with the display name first and the address between brackets afterwards.
How to display headers
As noted in the beginning of this article, and as displayed in the pictures of the mail client above, the recipient does not by default see the headers. However, most mail clients or webmail interfaces have an option to display the raw content received, including the headers.
Gmail
-
Click on the email you want to analyze, click on the three dots in the upper right corner, and select the
Show originaloption.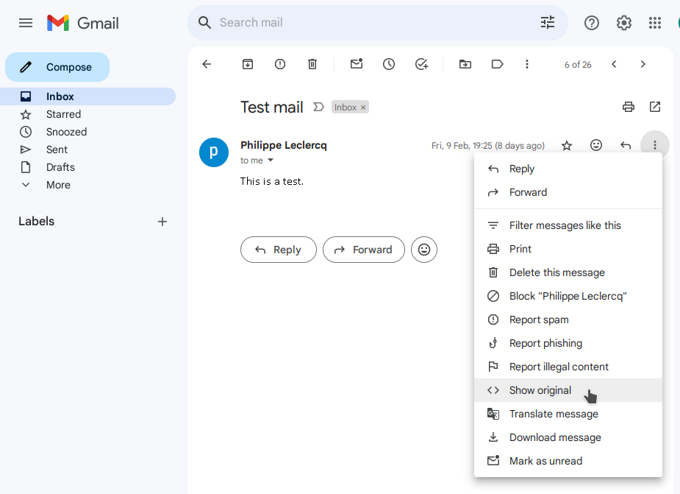
-
A new tab will open in the browser, showing the raw entire content of the email. You can copy it with the
Copy to clipboardbutton.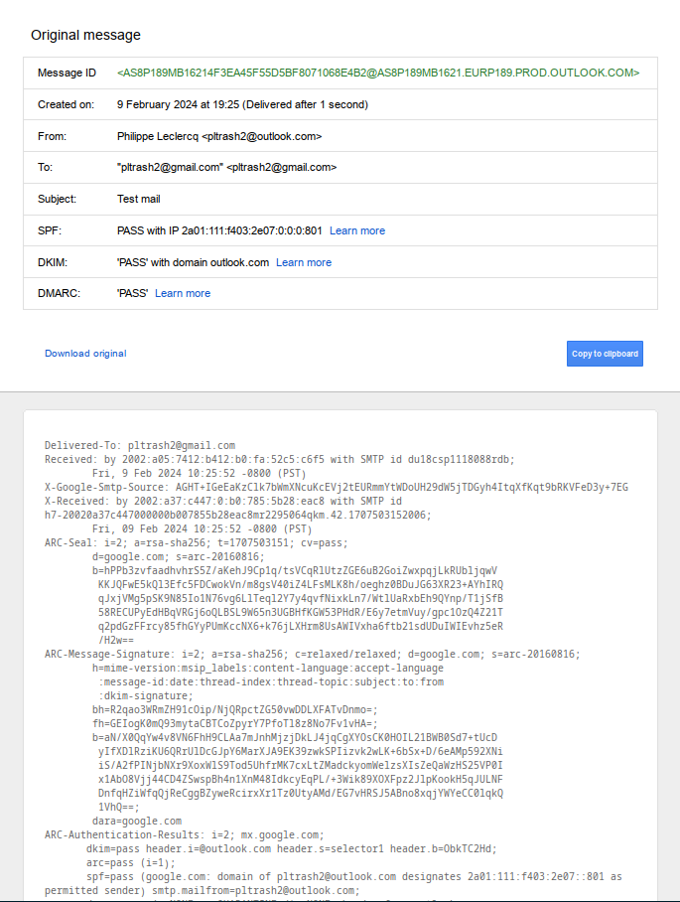
Microsoft Office 365
-
Select the email you want to analyze in the left pane.
-
Click on the three dots in the upper right corner, and select the
View -> View message detailsoption.
-
A new window will pop up in the browser, showing the raw entire content of the email.
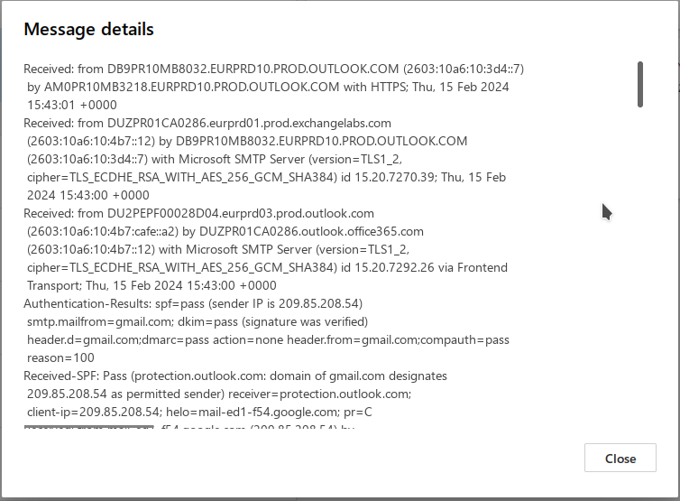
-
You can click in the window, select the whole text with <CTRL>-A, copy it with <CTRL>-C and paste it in another application (like a text editor) with <CTRL>-V.
Outlook
-
Double click on the email you want to analyze.
-
Click on
File -> Info -> Properties.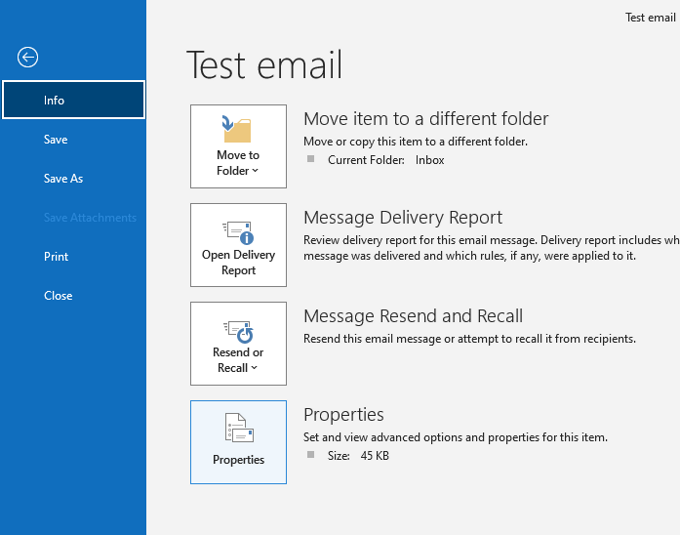
-
A property window will pop up, showing the Internet headers in the bottom text box.
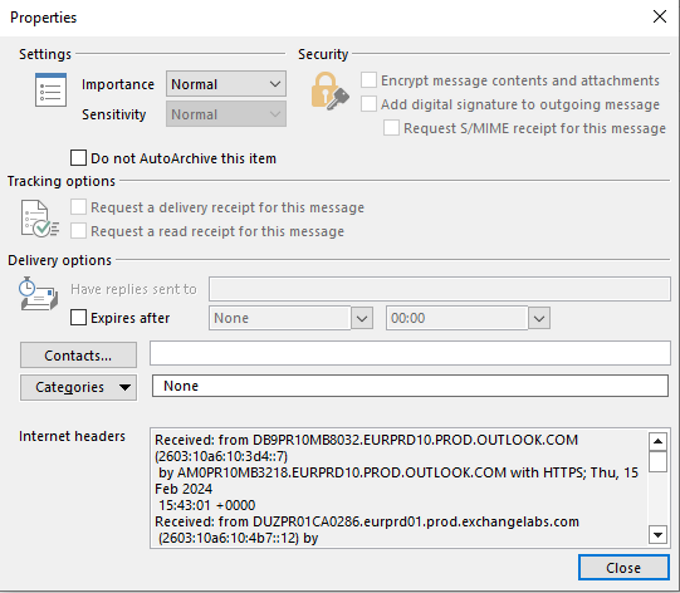
-
To copy the headers, click into the text box, select the whole text with <CTRL>-A, copy it with <CTRL>-C and paste it in another application (like a text editor) with <CTRL>-V.
Detecting potential fraudulent email by analyzing headers
Now, imagine you receive the following email:
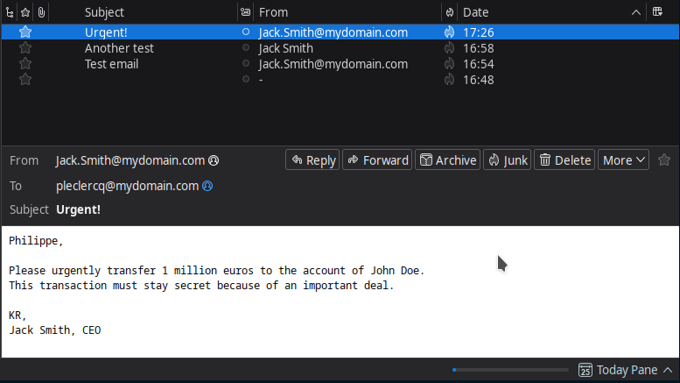
This is an unusual process, you are surprised. You try to call your Jack for confirmation, but he is abroad and unreachable. What to do next?
Well, let’s look at the headers:
From - Sun Feb 25 17:26:18 2024
X-Account-Key: account7
X-UIDL: 0000001165454373
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
X-Mozilla-Keys:
Return-Path: <attacker@evil.corp>
X-Original-To: pleclercq@mydomain.com
Delivered-To: pleclercq@mydomain.com
Received: from attacker?evil.corp (unknown [192.168.50.202])
by mailserver (Postfix) with SMTP id 054DC34DA
for <pleclercq@mydomain.com>; Sun, 25 Feb 2024 17:22:04 +0100 (CET)
From: Jack.Smith@mydomain.com
To: pleclercq@mydomain.com
Subject: Urgent!
Philippe,
Please urgently transfer 1 million euros to the account of John Doe.
This transaction must stay secret because of an important deal.
KR,
Jack Smith, CEO
Hmm. Return-Path: <attacker@evil.corp>.
This was NOT sent from Jack’s account, but by an attacker spoofing his address. Bad luck for them, you spotted it. Good on you!
Note
BTW, this is an example of a frequent abuse called CEO fraud or BEC - Business Email Compromise. According to Barclays Bank and the Treasurer Magazine, CEO fraud targets more than 400 companies a day, of which 40% are small and medium entreprises, triggering losses of more than 3 billion $.